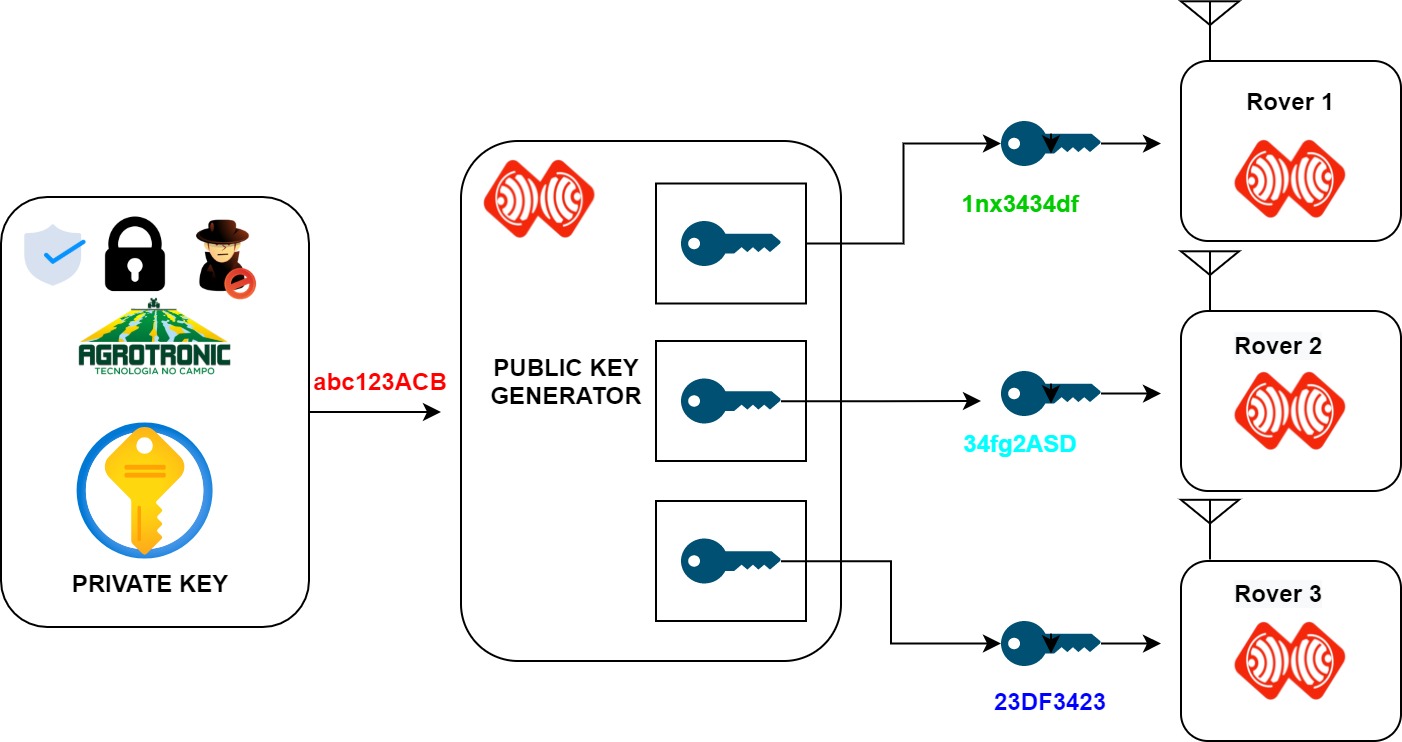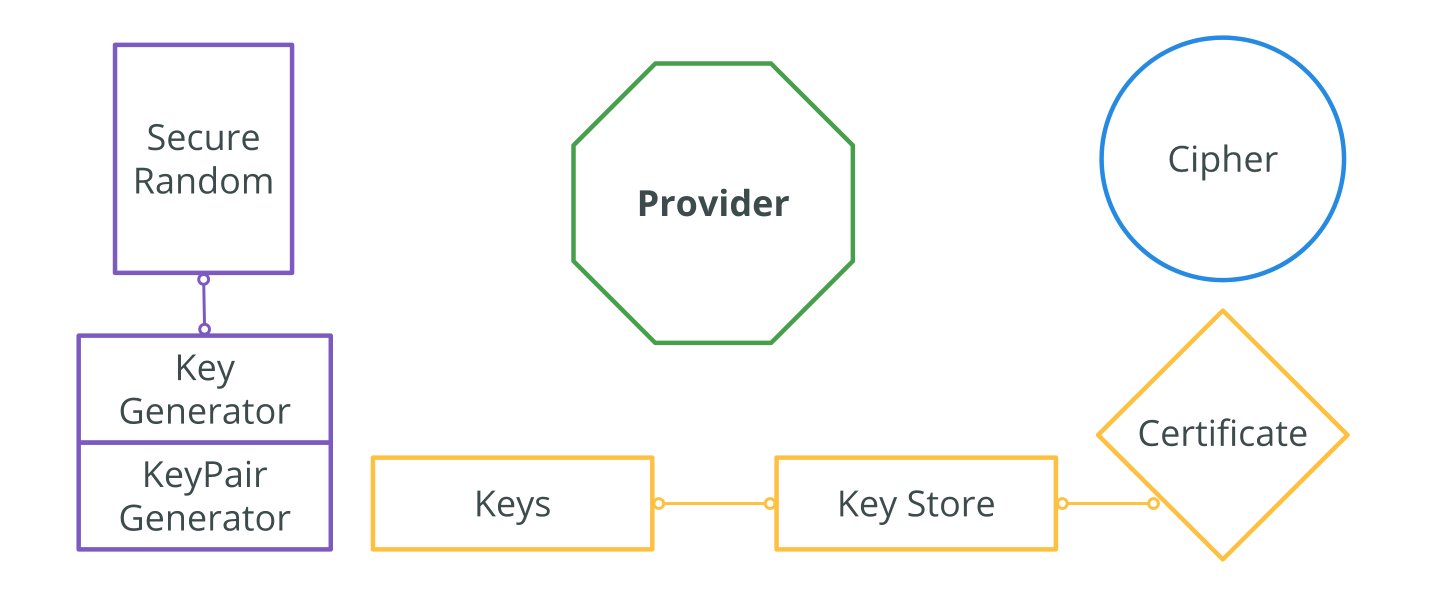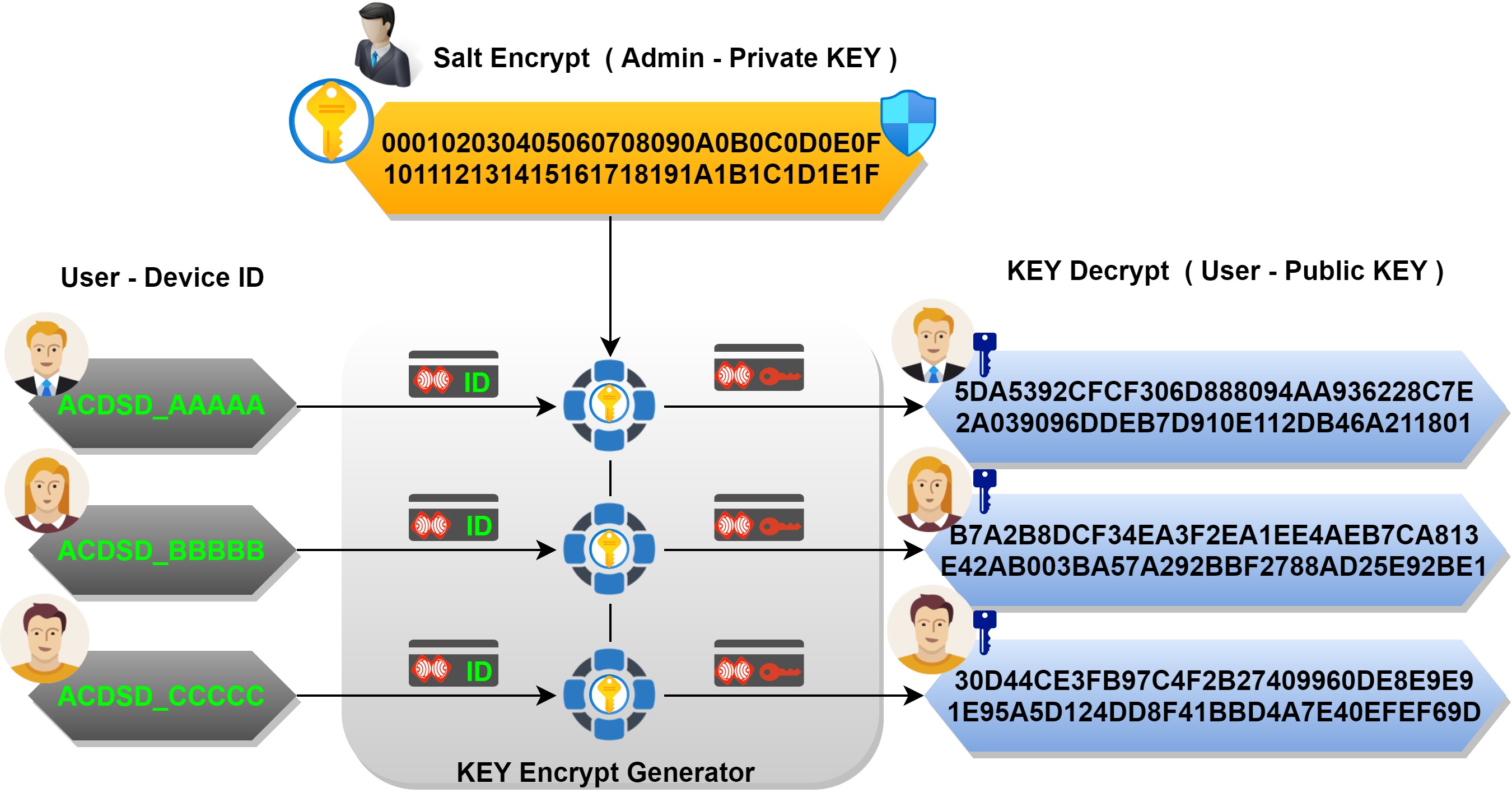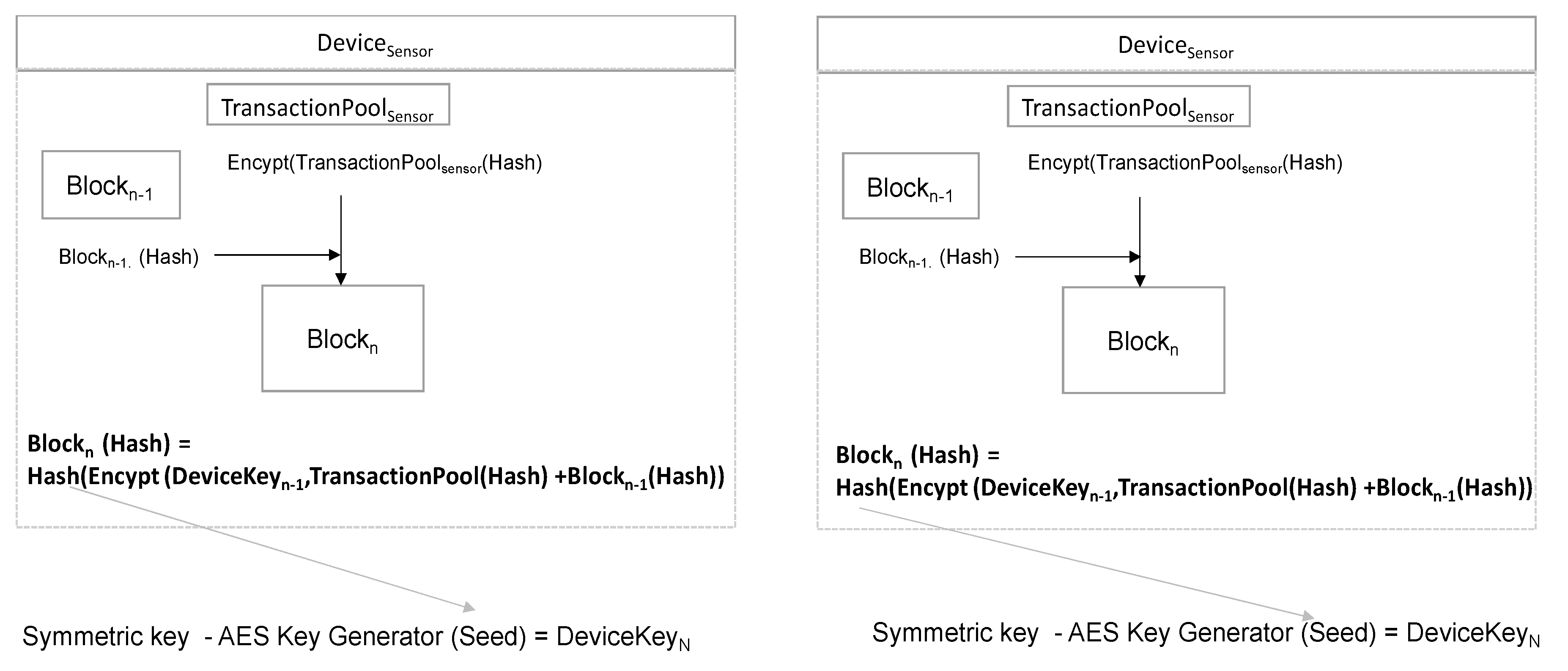
Applied Sciences | Free Full-Text | Block Data Record-Based Dynamic Encryption Key Generation Method for Security between Devices in Low Power Wireless Communication Environment of IoT

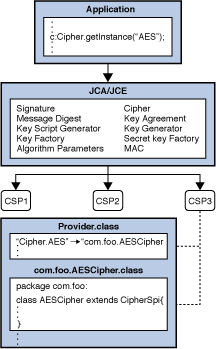
Generation of Cryptographic Keys from Personal Biometrics: An Illustration Based on Fingerprints | IntechOpen