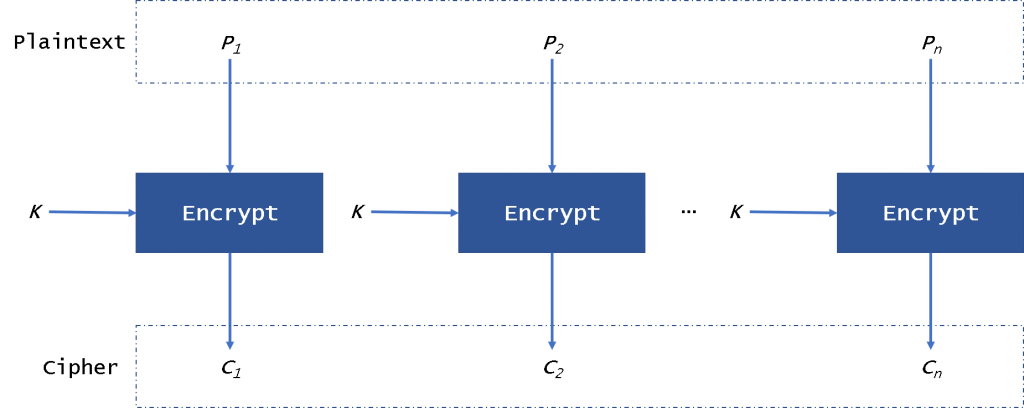
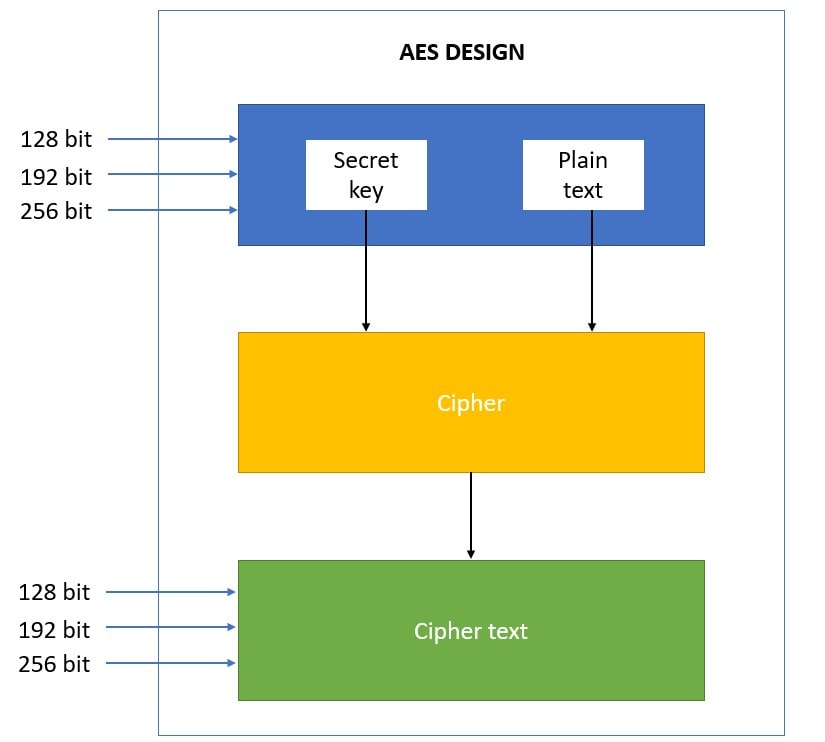
Electronics | Free Full-Text | Magniber v2 Ransomware Decryption: Exploiting the Vulnerability of a Self-Developed Pseudo Random Number Generator
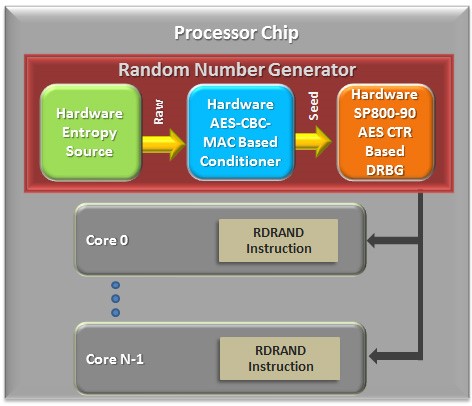
Intel® Hardware-based Security Technologies Bring Differentiation to Biometrics Recognition Applications Part 2 - CodeProject

Cryptopals: Exploiting CBC Padding Oracles | NCC Group Research Blog | Making the world safer and more secure
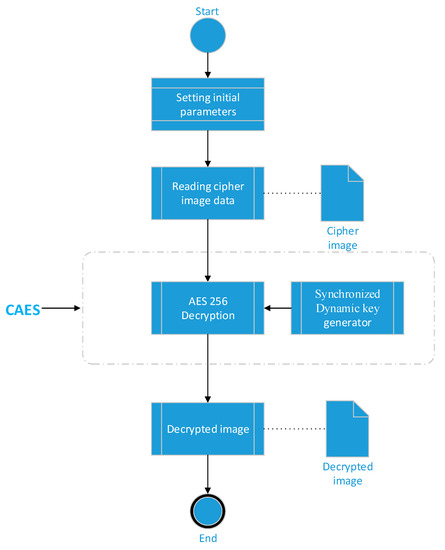
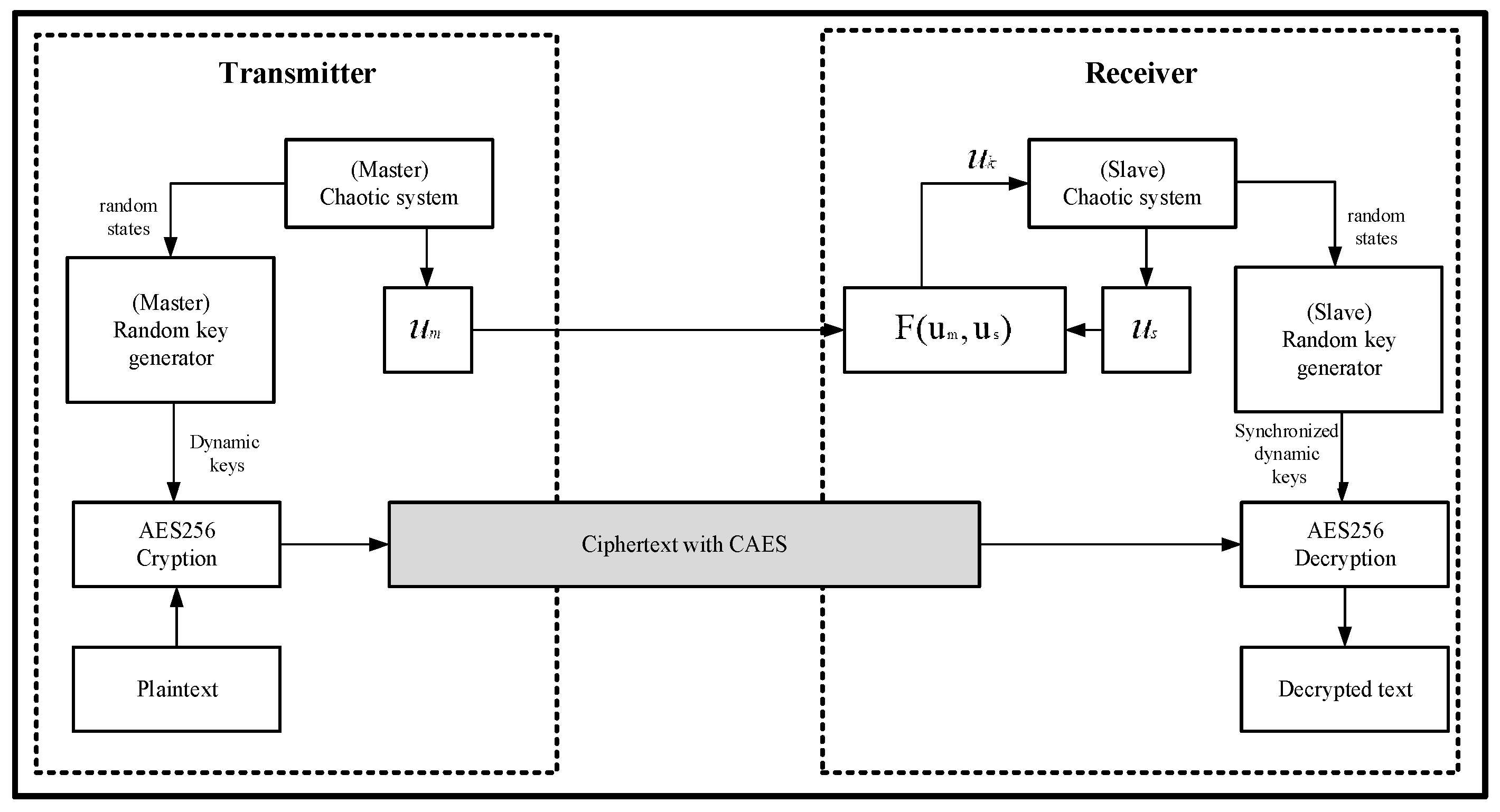
Applied Sciences | Free Full-Text | Chaos-Based Synchronized Dynamic Keys and Their Application to Image Encryption with an Improved AES Algorithm